Technical Roadmaps
From its conception, Flow was architected to be fully decentralized and Byzantine Fault Tolerant [5, 6, 7]. The Flow team has adopted an evolutionary approach to the protocol implementation, incrementally opening up the platform while eliminating implementation shortcuts that still rely on humans for security. This page will summarize the major milestones towards full protocol autonomy and BFT for the Flow network. To date, Flow has achieved decentralization and is systematically enabling permissionless participation across all node types. Through strategic technological advancements, Flow continues to bolster its resilience against adversarial behavior while maintaining network integrity for production use-cases and continuing to scale throughput, speed, storage capacity and interoperability with other crypto networks.
Flow Protocol Autonomy: Current State and Progress
The decentralized nature and intrinsic resilience of crypto networks to malicious infrastructure operators (known as "nodes") offer significant advantages over conventional computing platforms, such as cloud instances. These advantages include improved resistance to malware, cyber warfare, natural disasters, political and economic power struggles, vendor lock-in, and restrictions on API and data access.
Decentralization refers to a network's ability to function without relying on any single entity, business, or interest group. Even if a group of participants ceases operation, a decentralized network maintains availability and correctness. Geographical distribution of nodes is crucial for this purpose, enhancing the network's resilience against natural disasters, conflicts, pandemics, and authoritarian regimes. In other words, if nodes provide the network's hardware capabilities, decentralization measures the resilience of this hardware layer.
In addition, the software running on each node, where protocol rules are implemented, must effectively handle malicious messages from other nodes. Analogous to decentralization for the hardware layer, ‘Byzantine Fault Tolerance’ [BFT] [1, 2] measures resilience at the software layer, especially in the presence of adversarial infrastructure operators (Byzantine nodes). An established limit for BFT consensus is the “⅓ threshold”: if ⅓ or more nodes in the consensus committee are Byzantine, they can compromise the network.
Most modern crypto networks use staking of network tokens to prevent sybil attacks and economically enforce protocol-compliant behavior (Proof of Stake). Through staking, each network has a specified notion of “authorized participants” for each of block. BFT research focuses on potentially malicious and colluding nodes within the staked network.
Intuitively, we measure a network's byzantine fault tolerance on a pareto frontier by answering questions such as: 1. Liveness: How many nodes can be offline (or maliciously abstain from participating) without (significantly) impacting availability; and 2. Safety: How many (potentially colluding) nodes are required to convince an honest node to accept a wrong result.
Beyond tolerating attacks, the next evolutionary step is counteracting and punishing adversarial behavior (suppress and slash) automatically. At the time of writing, many established Proof of Stake networks [3] [4] rely on human intervention for suppression, attribution, and slashing in cases of actively malicious behavior by staked nodes. The Flow ecosystem has rejected these approaches as risky and unreasonably optimistic. Instead, by ensuring that all node operators are known to and vetted by the community, Flow aims to be more resilient to a number of realistic attack scenarios for the short term until all reasonable technical countermeasures are in place.
Network decentralization and autonomy are best described on a spectrum rather than as a binary classification of absent or present. At one end, we have highly centralized networks, while at the other, fully decentralized and autonomously BFT networks. Typically, networks start smaller and more centralized, gradually evolving towards greater decentralization and autonomy. Flow is following this natural progression.
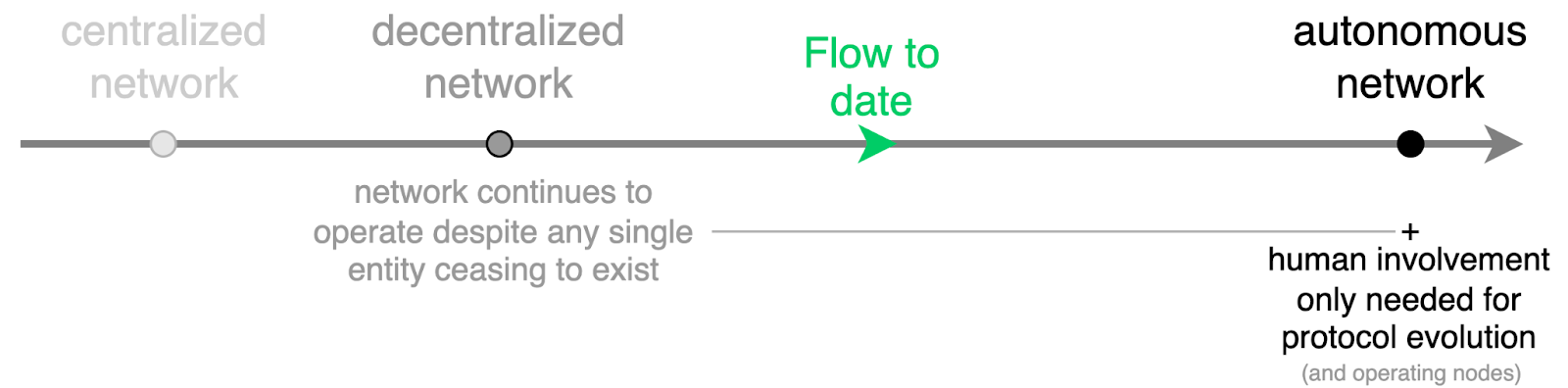
Since its genesis in 2020, Flow has reached several significant milestones that reinforce its decentralized nature and technical robustness:
- 2021 - Decentralized Operation: Since the end of 2021, the Flow consensus committee has been fully decentralized, with each participant controlling less than one-third of the voting power for block generation. This prevents any single entity from halting the central consensus process, which serves as the security authority in the network and orchestrates the Flow transaction processing pipeline. Governance is managed through a multisig approach, requiring protocol adjustments to be approved and signed by a diverse board of node operators and community representatives.
- 2022 - Permissionless Smart Contract Deployment: Initially, the Cadence programming language and virtual machine on Flow were not fully resilient against malicious smart contracts, requiring teams to submit their code for an audit before deployment. In July 2022, the hardening of the smart contract execution environment on Flow was completed, opening Flow for permissionless smart contract deployment.
- 2022 - Resilience Against Impersonation and Masquerade Attacks: In 2022, Flow enhanced its defenses against identity-based threats. The network's multi-node, pipelined architecture – foundational for its unmatched scalability and efficiency – now includes robust protections against impersonation and masquerade attacks [8].
- 2022 - Permissionless Access Nodes: At the end of 2022, Flow introduced permissionless Access Nodes, marking the first step towards fully permissionless participation. By staking and running their own Access Nodes without needing approval from the governance committee, community participants, such as developers and exchanges, can access all chain data securely and trustlessly, without relying on centralized data providers [9].
- 2023 - BFT Consensus: Flow uses HotStuff, a BFT consensus algorithm with mathematically proven liveness and security. From the outset, the Flow implementation of HotStuff detects all consensus violations and records the corresponding cryptographic evidence. Early 2023, the Jolteon extension for HotStuff was rolled out to Flow Mainnet [10], fortifying the network against timing attacks, enhancing stability, and accelerating transaction finalization by 33%.
- 2023 - Consensus Follower: While Flow Consensus Nodes actively extend the chain by proposing and voting on new blocks, other node roles—such as Collector, Execution, Verification, and Access Nodes—merely observe and locally verify consensus. This lightweight logic for tracking consensus progression without active participation is implemented in the Consensus Follower software library. In June 2023, this library received a major upgrade, enhancing its resilience against attacks and improving processing speed [11], thereby shielding higher-level processing logic from malicious nodes sending invalid blocks. Additionally, it laid the foundation for future light clients, ensuring robust performance, security, and trustless data access for all clients of the Flow network, even on smartphones.
- 2023 - Cryptographically Secure Randomness: Since its inception, Flow has a BFT random number generator [6, 12]. As of August 2023, fast and secure randomness on Flow is available natively for smart contracts [13], avoiding the complexity and bug-propensity inherent to third party oracles.
- 2023 - BFT Testing Framework: In 2023, we implemented the only framework of its type in existence for testing a blockchain's resilience against coordinated attacks by groups of colluding nodes [14].
- 2023 - Flow Foundation: Flow originated as an R&D project from Dapper Labs during the time when CryptoKitties massively congested Ethereum. In October 2021, the Flow Foundation was established as a non-profit organization dedicated to the prosperity of the entire Flow ecosystem. By 2023, Flow engineering transitioned from Dapper Labs to the Flow Foundation, and the nodes maintained jointly by Dapper and the Foundation were operationally separated. This transition matured Flow into an impartial and organizationally independent platform.
- 2024 - BFT Networking Layer: Since early 2024, the Flow networking layer is more robust than most L1s, with the ability to withstand coordinated attacks from multiple colluding nodes, and substantial resilience against non-colluding malicious nodes that might attempt to spam the network to create a denial of service (DoS) attack. Defense mechanisms include a unified peer-scoring algorithm [15] for ranking nodes based on reliability and responsiveness of data delivery, spam and replay mitigations [16]. Additionally, tooling was added for node operators to manually blacklist nodes to defend against attacks not yet automatically handled.
- 2024 - Dynamic Protocol State for Quickly Banning Misbehaving Nodes: Dynamic Protocol State reached mainnet as part of the Crescendo upgrade. Thanks to this upgrade, adaptability and security are enhanced on Flow through dynamic identity management, including mechanisms for quickly slashing and banning misbehaving nodes. Additionally, the Dynamic Protocol State includes a framework for algorithmically adjusting protocol parameters and updating auxiliary status data. This major advancement strengthens the autonomy of Flow in mitigating security threats and adapting to challenging operational environments. [17]
These achievements underscore the commitment of Flow to security, decentralization, and network autonomy.
Prioritizing Networking Security and Efficient Scaling
Significant advancements in blockchain scalability and efficiency require moving beyond monolithic architectures [5, 18]. Monolithic blockchains — systems built from a single type of node — keep design complexity low, as each node performs the same tasks: verifying block proposals and confirming final results. However, this simplicity has inherent trade-offs, forcing compromises between scalability, security, and decentralization [19].
Flow consists of five individual node types, each with specialized hardware requirements and its own set of tasks. This allows Flow to balance the competing factors of decentralization, throughput, and security appropriately for each node type, maximizing all three aspects for the network while reducing energy and hardware requirements by 10.
Most aspirational software creators and companies aim to engage a large user base. A strong safety emphasis on safety, paired with mainstream developer- and user-friendliness, differentiates Flow from other blockchains.
At Flow, we proudly prioritize users' and developers' security and accept longer timelines over prematurely opening the network for the benefit of marketing and hype. Flow addresses security, scalability, and usability challenges all at the protocol level, enabling developers to innovate and deploy creative, technically sophisticated projects while ensuring the security of users' assets and data.
Implementing Permissionless Participation on Flow
In precise technical terms, permissionless participation means that nodes can join the network after successfully completing an anonymous, purely algorithmic staking process that is open to everyone, without requiring explicit approval from a human governance committee. Permissionlessly participating nodes on Flow must stake a given minimum stake amount and submit their node's public keys (and optionally an email address to receive protocol upgrade notifications in the future) through a few staking transactions.
The State of Permissionless Participation on Flow
The first permissionlessly participating nodes on Flow were Access Nodes. Access Nodes on Flow route transactions and provide trustless access to state and transaction results, without being directly involved in block production, execution, or verification. Hence, there are limited attack vectors for Byzantine Access Nodes, with the most severe being Impersonation and Masquerade Attacks, both of which were covered before the first permissionless Access Nodes joined the network in 2022. Initially, the network had limited tolerance against coordinated spamming or eclipse attacks, so security was prioritized and the number of permissionless Access Nodes allowed to stake was gradually increased each month.
Today, the Flow networking layer is robust, able to withstand coordinated attacks from multiple colluding nodes, and substantial resilience against non-colluding malicious nodes that might attempt to spam the network to create a DoS attack. Additionally, manual fallbacks are in place to defend against attacks that have not yet been automatically handled. For a larger number of staked nodes, it is generally assumed that only a minority is Byzantine. Therefore, it is believed that the Flow networking layer is prepared for broader permissionless participation, with current efforts directed toward making the node-specific logic fully Byzantine Fault Tolerant (BFT).
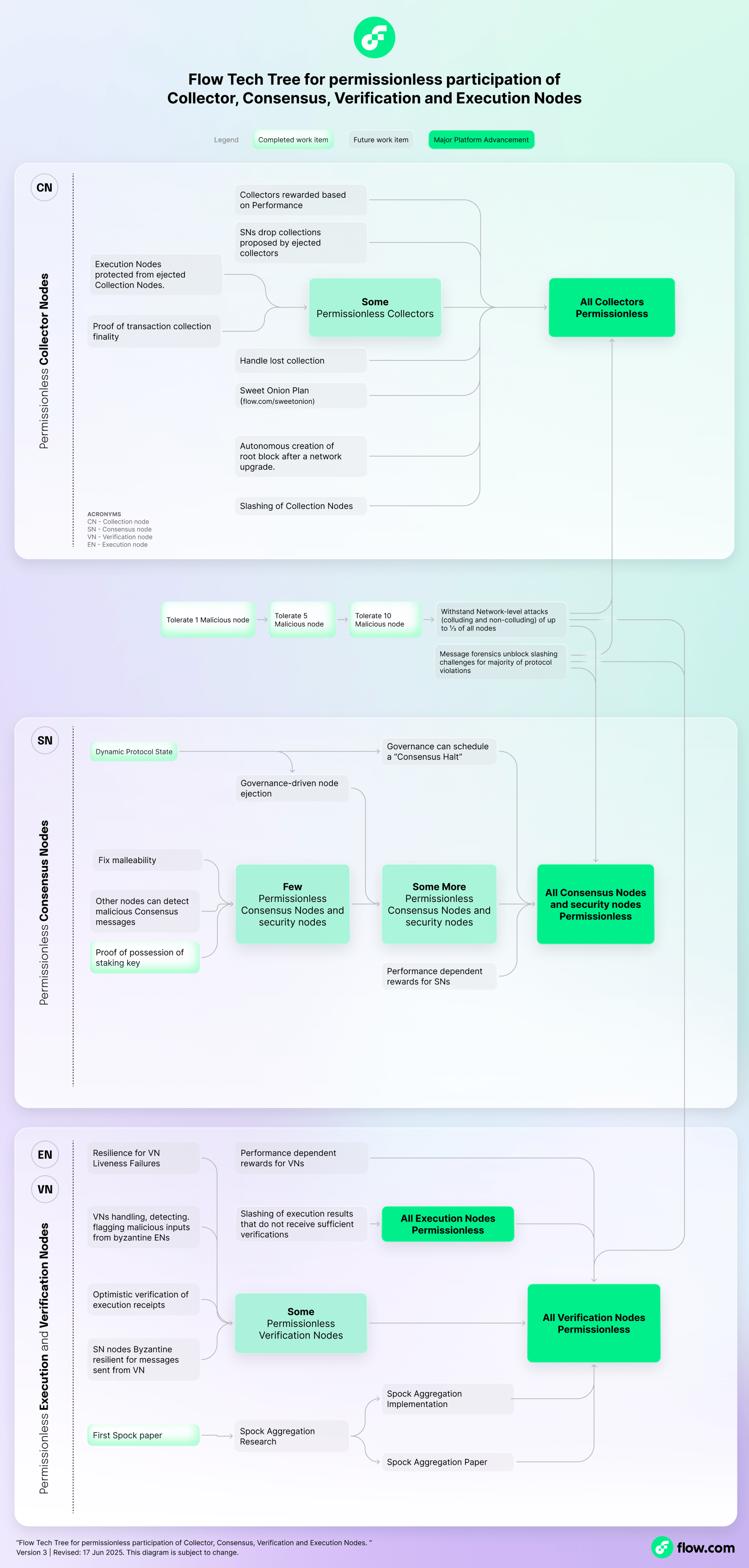
Flow Collector Nodes form a horizontally scaling data-availability layer: they collect incoming transactions and group them into batches called ‘collections’. Collections are sent directly to the Execution and Access Nodes, while Consensus Nodes reference the collections in their blocks by hash [6]. The need for nodes to gracefully handle malformed messages from Collectors, slashing, and performance-dependent rewards are analogous to the other node roles. Beyond that, the remaining work for permissionless collector participation is limited to the following.
Proof of Collection Finality
Groups of collectors (known as ‘collector clusters’) use a mini-version of HotStuff to agree on which transactions to include in their collections. This ensures robust data availability and mitigates resource exhaustion attacks by preventing individual collectors from including garbage or repetitive transactions. As long as the fraction of Byzantine collectors in each cluster is less than one-third, malicious collections proposed by permissionless collectors will not be finalized by the cluster consensus, and the proposing collector will eventually be slashed. With only honest collectors, Consensus Nodes can currently trust that any collection submitted for inclusion in a block is indeed finalized as prescribed by the protocol. Before admitting permissionless collectors, this shortcut must be removed by adding proofs of collection finality.
Remove Centralized Initialization of Collector Clusters After Major Network Upgrades
Every week (referred to as an ‘epoch’), nodes can join or leave the Flow network at predefined points. Before a new epoch starts, the protocol randomly partitions all Collector Nodes participating in this epoch into new clusters. At initialization, each cluster requires a root collection as a starting point for their cluster consensus, and these root collections need to be signed by a supermajority of the collectors in the respective cluster (similar to a genesis block when starting a new chain).
While the network is running, Collector Nodes use a smart contract to generate the root collections and gather their signatures. However, during major protocol upgrades, the network is temporarily stopped and restarted with the new version of the protocol, meaning there is not at that time a running network to generate the root collections. During these major upgrades, the Flow Foundation currently gathers the collector signatures and disseminates the root collections back to the collector clusters to enable them to start. The protocol’s dependence on the Flow Foundation as a coordinator of these network upgrades will be progressively reduced over time.
Achieving broader permissionless participation necessitates that nodes, particularly those involved in consensus, are resilient against all possible attacks. While the Flow implementation of HotStuff-Jolteon [10] and Consensus Follower [11] already provide robust BFT, further engineering efforts are required for other components. These range from minor tweaks to major overhauls.
Below, we briefly summarize the highest-priority work streams for permissionless consensus participation:
Hardening the Staking Process with Proof of Possession
Proof of Possession [PoP] is a critical mechanism for the security of protocol signatures: a new node wanting to stake must prove it owns the private key corresponding to the public key it submits in the staking transaction [23]. Without PoPs, a malicious participant can fake a block attestation or a result approval.
Prevent Byzantine Nodes from Modifying Relayed Messages
At the moment, there are malleability edge cases with Flow blocks and other messages that nodes exchange. This does not pose an immediate threat since Consensus, Verification, and Collector Nodes are currently run by credible operators and are hence non-byzantine. However, it is crucial to close the malleability surface before enabling permissionless participation for these node types to prevent undetected propagation of incorrect data. In the future, verified data sharing among Access Nodes and trustless light clients will be ensured, requiring the resolution of malleability issues.
Automated Performance Incentives and Slashing
Flow uses rewards and financial penalties to incentivize availability, throughput, speed, correctness, and safety. The HotStuff-Jolteon implementation on Flow already detects and records all consensus violations, but adjudication and punishment currently rely on human governance. In the future, Message Forensics will enable nodes to conclusively prove fault for malicious messages and automated adjudication of slashing challenges and ejection of misbehaving nodes will be enabled. Overall, this work will drastically shorten attack windows and enable Flow to autonomously suppress attacks.
In practice, slow or unresponsive nodes are more common than malicious participants. Performance-Dependent Rewards mitigate this challenge: fast and reliable nodes receive higher compensation, while significantly underperforming nodes receive minimal rewards. This system discourages freeloaders and incentivizes high service levels.
Hardening Against Malformed Messages from Consensus Nodes
For permissionless consensus participation, it is essential to harden all nodes' business logic against malformed messages from Consensus Nodes. While the HotStuff-Jolteon implementation on Flow is already BFT, it only inspects block headers, leaving some residual surface for malformed block payloads and other messages, such as synchronization requests to re-send data. The existing message-inspection framework, which currently protects against malicious Access Nodes, will be extended to include additional checks for consensus messages.
Resilience to Unresponsive or Malicious Verification Nodes
Extensive Checking Mode is crucial for the resilience of Flow against unresponsive verifiers, ensuring that a correct result receives the necessary verification approvals to be committed (sealed). In cases involving unresponsive verifiers, Consensus Nodes engage Extensive Checking Mode to incrementally expand the verifier set assigned to check the execution result. In the worst-case scenario, where ⅓ of verifiers are maliciously colluding with an Execution Node publishing an incorrect result, 100% of verifiers might eventually need to check the results. In monolithic blockchains, this "worst-case" cost of all nodes executing every transaction is the default. Comparatively, with a lower fraction of Byzantine verifiers (the overwhelmingly likely scenario), the probability of the worst-case verification cost in Flow exponentially decreases, making Flow an order of magnitude more energy and hardware-efficient than monolithic architectures.
While implementing Extensive Checking Mode on Consensus Nodes is relatively straightforward, adding the corresponding logic to Verification Nodes will require a larger-scale software revision. This would be most efficient if done alongside strategic performance improvements to Verification Nodes, enabling for optimistic verification of unfinalized forks (significant latency improvements) and resilience against malicious inputs from prospective Byzantine Execution Nodes (working towards permissionless Execution Nodes).
In some areas, the work on permissionless consensus participation naturally extends to Permissionless Verification Nodes, such as Extensive Checking Mode, Slashing, Performance-Dependent Rewards, and resilience to malicious messages from Verification Nodes. Additionally, there are clear work streams specific to Verification Nodes, summarized below. Interested readers can refer to the Verification Node Roadmap for further details.
Faster Verification of Execution Results
Optimistic verification allows Verification Nodes to check the execution results for unfinalized blocks. This enhances network efficiency and improves the overall user experience by speeding up transaction confirmations.
Scaling the Flow Solution to the Verifier's Dilemma to Thousands of Nodes
Specialized Proof of Confidential Knowledge [SPoCK] is a novel cryptographic technique [24] that Flow uses to solve the Verifier’s Dilemma inherent to blockchains. The Verifier's Dilemma states that in blockchains with few cheaters, verifiers are incentivized to rubber-stamp all results as correct rather than perform costly verification [25].
At maturity, Flow aims to have over 1000 Verification Nodes, each checking about 8% of a block's computation. When included individually in a block, the proofs confirming that enough Verification Nodes actually confirmed the computation would consume roughly 3MB, exceeding the current 1MB block size limit for fast consensus. Since the Flow implementation of SPoCK is based on the BLS scheme [26], it can likely also be aggregated, reducing data size and improving efficiency. Formal security proofs for peer-reviewed publication are currently being worked on, followed by implementation.
At present, the Flow network will benefit most from enabling permissionless participation of Consensus, Verification, and Collector Nodes while increasing the seats for permissionless Access Nodes. Due to their significant hardware requirements and the deterministic nature of their work, enabling permissionless participation of Execution Nodes will likely be one of the later steps.
Further Reading
- For readers wanting to better understand how the Flow architecture enables groundbreaking horizontal scalability and efficiency, the Core Protocol Vision will be particularly interesting.
- The BFT Master Plan contains a detailed list of engineering and implementation steps for the Flow protocol to be completed with respect to BFT and robustness against unfavorable operating conditions.
- The planned revisions for the Verification Node, which combine major latency improvements with Extensive Checking Mode and the remaining major Byzantine protections, are specified in detail in the documents Verification Node Roadmap and Recommendations for Verifier Design.
References
- [1] The Byzantine Generals Problem, Lamport, Shostak, Pease, 1982
- [2] Byzantine fault (wikipedia)
- [3] Solana's documentation on Optimistic Confirmation and Slashing
- [Quote] “for regular consensus, after a safety violation, the network will halt. We can analyze the data and figure out who was responsible and propose that the stake should be slashed after restart.
- [4] Aptos documentation on Staking
- [5] Flow: Separating Consensus and Compute, arXiv:1909.05821, 2019
- [6] Flow: Separating Consensus and Compute – Block Formation and Execution, arXiv:2002.07403, 2020
- [7] Flow: Separating Consensus and Compute – Execution Verification, arXiv:1909.05832, 2019
- [8] impersonation & masquerade slashing hooks
- [9] Introducing Observer Nodes, a new permissionless node type on Flow and Setting Up a Flow Access Node
- [10] Jolteon: Advancing Flow’s consensus algorithm, 2023
- [11] Upgrading Flow Consensus Follower to boost attack resilience and processing speed, 2023
- [12] Secure random number generator for Flow smart contracts
- [13] Randomness on FLOW
- [14] BFT Testing Framework for Flow Blockchain, by Y. Hassanzadeh-Nazarabadi, M. Rybalov, K. Claybon; International Congress on Blockchain and Applications 2023 (Conf. proc. LNNS volume 778; conf. talk youtube)
- [15] Flow documentation on GossipSub App Specific Score
- [16] Flow documentation on Control Message Validation Inspector Overview
- [17] Dynamic Protocol State as building block for Byzantine Fault Tolerance [BFT] and an autonomously-operating Flow-network, 2023
- [18] Flow Core-Protocol Vision, 2023
- [19] Modular vs. Monolithic Blockchains, alchemy 2022
- [20] Inside Flow: The Multi-Node Architecture that Scales to Millions, 2021
- [21] Halting the Solana Blockchain with Epsilon Stake, by Q Kniep, F Schaich, J Sliwinski, R Wattenhofer; Int. Conf. Distributed Computing and Networking 2024 (doi)
- [22] Proof of history: what is it good for?, V. Shoup, 2022
- [23] Upgrading Ethereum - A technical handbook on Ethereum's move to proof of stake and beyond, Edition 0.3: Capella [WIP], Sept 2023
- [24] Flow: Specialized Proof of Confidential Knowledge (SPoCK), 2020
- [25] Demystifying incentives in the consensus computer, by L. Luu, J. Teutsch, R. Kulkarni, P. Saxena, Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, 2015
- [26] Short signatures from the Weil pairing by D. Boneh, B. Lynn, H. Shacham, ASIACRYPT, 2001.
Stay up to date with the latest news on Flow.
Stay up to date with the latest news on Flow.


